smart-card wifi authentication This article presents information about commonly used different ways to configure Extensible Authentication Protocol (EAP) settings. Specifically, it describes configuring EAP profiles using XML and command line tools. It also shows how to configure EAP settings and profiles using various UI in Windows. See more Payment terminals use NFC so your smartphone essentially emulates the data stored on your card. Only the account holder can add their card because the process involves authentication with the bank .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Follow these simple steps to scan NFC Tags with an Android Phone. To learn .
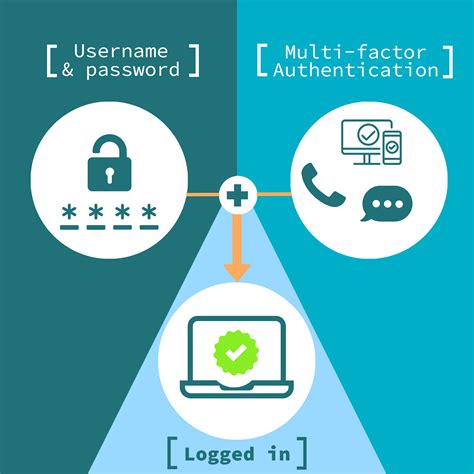
This article presents information about commonly used different ways to configure Extensible Authentication Protocol (EAP) settings. Specifically, it describes configuring EAP profiles using XML and command line tools. It also shows how to configure EAP settings and profiles using various UI in Windows. See more
Using EAP-TLS authentication method allows users to authenticate on the Access Point using a client authentication certificate. Via Windows wifi . This article presents information about commonly used different ways to configure Extensible Authentication Protocol (EAP) settings. Specifically, it describes configuring EAP profiles using XML and command line tools. It also shows how to configure EAP settings and profiles using various UI in Windows.
Using EAP-TLS authentication method allows users to authenticate on the Access Point using a client authentication certificate. Via Windows wifi properties, you can choose "Smart Card or other Certificate Properties" tab in order to specify a certificate.
This article contains configuration information specific to the following authentication methods in EAP. EAP-Transport Layer Security (EAP-TLS): Standards-based EAP method that uses TLS with certificates for mutual authentication. Appears as Smart Card or other Certificate (EAP-TLS) in Windows.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. GPO for Wireless settings. The following settings were configured in GPO to apply Wireless 802.11 settings to some test clients. In a GPO: Computer configuration > Policies > Windows settings > Security settings > Wireless Network IEEE (802.11) Settings.What is a PKI? Passwords can be lost, stolen, forgotten, and shared around, making any credential-based network vulnerable to over-the-air credential theft. Certificates provide a more secure form of network authentication than passwords because they are .
Assuming you already have a functional 802.1x Wi-Fi setup, you should have at least one Network Policy within NPS. Make sure that one of the authentication methods for this is "Microsoft: Smart Card or other certificate". Windows 22H2 depricates 802.1x authentication over MS-SCHAPv2 - here's how to use EAP-TLS instead. I spent a couple of day tidying up this process, so hopefully it helps some of you out and saves you some time.
With an embedded microcontroller, smart cards have the unique ability to store large amounts of data, carry out their own on-card functions (e.g., encryption and mutual authentication) and interact intelligently with a smart card reader.
smart card multi factor authentication
smart card identity
v1ce contactless business card
An 802.1x WLAN first requires wireless clients to authenticate through the AP to a RADIUS server, then lets the AP and wireless client negotiate dynamic encryption keys instead of using the much weaker static keys that most WEP networks use. This article presents information about commonly used different ways to configure Extensible Authentication Protocol (EAP) settings. Specifically, it describes configuring EAP profiles using XML and command line tools. It also shows how to configure EAP settings and profiles using various UI in Windows.Using EAP-TLS authentication method allows users to authenticate on the Access Point using a client authentication certificate. Via Windows wifi properties, you can choose "Smart Card or other Certificate Properties" tab in order to specify a certificate.
This article contains configuration information specific to the following authentication methods in EAP. EAP-Transport Layer Security (EAP-TLS): Standards-based EAP method that uses TLS with certificates for mutual authentication. Appears as Smart Card or other Certificate (EAP-TLS) in Windows.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. GPO for Wireless settings. The following settings were configured in GPO to apply Wireless 802.11 settings to some test clients. In a GPO: Computer configuration > Policies > Windows settings > Security settings > Wireless Network IEEE (802.11) Settings.
What is a PKI? Passwords can be lost, stolen, forgotten, and shared around, making any credential-based network vulnerable to over-the-air credential theft. Certificates provide a more secure form of network authentication than passwords because they are . Assuming you already have a functional 802.1x Wi-Fi setup, you should have at least one Network Policy within NPS. Make sure that one of the authentication methods for this is "Microsoft: Smart Card or other certificate".
Windows 22H2 depricates 802.1x authentication over MS-SCHAPv2 - here's how to use EAP-TLS instead. I spent a couple of day tidying up this process, so hopefully it helps some of you out and saves you some time.
With an embedded microcontroller, smart cards have the unique ability to store large amounts of data, carry out their own on-card functions (e.g., encryption and mutual authentication) and interact intelligently with a smart card reader.
what is the range of a contactless card
smart card based identification system
Suitable for terminal login authentication, etc., using IC cards in major virtualization systems to realize secure thin client environments. For details of environments, refer to the thin client . See more
smart-card wifi authentication|authenticate using your smart card