how to hack a mifare card • Initially utilize the MFOC tool to test if the card utilize any default keys. (around 10 minutes) – . Your business card Put your contact info directly onto customers’ devices with your smart business card. Your customers People hold their phone over the card to activate the phone’s . See more
0 · How to hack Mifare Classic NFC cards
1 · Hacking Mifare Classic Cards
2 · Hacking MIFARE & RFID
3 · Cracking The MiFare Classic Could Get You Free Snacks
Within each conference, the four division winners and the top two non-division winners with the best overall regular season records) qualified . See more
MIFARE, is a trademark for a series of chips widely used in contactless smart .
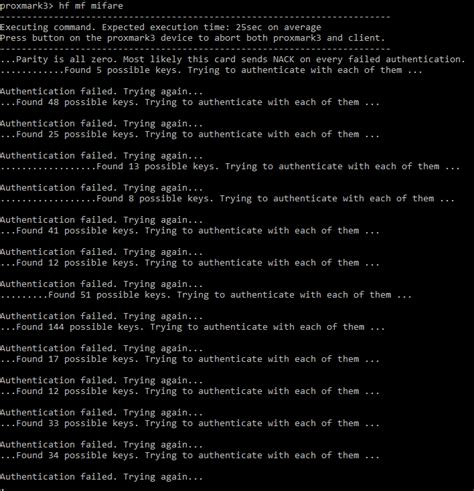
In Figure 2.2, I have launched a MFOC attack, asking the tool to dump the memory of the ta.Hacking our first MIFAR/RFID Tag. by phantasmthewhite | Feb 1, 2019 | hacking. Easy tutori. There’s plenty of guides online on how to crack the private keys that are .• Initially utilize the MFOC tool to test if the card utilize any default keys. (around 10 minutes) – .
First Key Recovery. CRYPTO-1 uses two 48 bits-long keys on Mifare Classic cards to encrypt the data on its sectors. Each key can be .
MIFARE, is a trademark for a series of chips widely used in contactless smart cards and proximity cards. It is often incorrectly used as a synonym of RFID. MIFARE is owned by NXP semiconductors which was previously known as Philips Electronics. The reason behind this misuse is simple. There’s plenty of guides online on how to crack the private keys that are supposed to make the card secure. Conveniently, [Guillermo] had a reader/writer on hand for these very cards..
is wild card the playoffs
How to hack Mifare Classic NFC cards
• Initially utilize the MFOC tool to test if the card utilize any default keys. (around 10 minutes) – If the card utilizes any of default keys the MFOC tool will perform the Nested attack utilizing any authenticated sector as an exploit sector to recover all keys of the card and dump his content. First Key Recovery. CRYPTO-1 uses two 48 bits-long keys on Mifare Classic cards to encrypt the data on its sectors. Each key can be configured to be used for reading or writing on a sector. On. The first attack on Mifare cards is called Darkside attack, which exploit the weak pseudo-random generator on the card to discover a single key. This attack aims to recover one key from the.How to Crack Mifare 1k RFID card. The NFC tag I analyzed is a so called “Mifare Classic 1k” tag. 1k stands for the size of data the tag can store. There are also other types like the “Mifare Classic 4k” and the “Mifare Mini” each having a different memory size. A Mifare Classic 1k tag contains 16 sectors. Each of these sectors has 3 .
New Design RFID-PN532: https://shop.mtoolstec.com0:00 Quick look on the phone and card for testing.0:30 Read original data with Mifare Classic Tool0:56 Read . Mifare Classic in general is stated insecure, because it’s encryption protocol has been cracked. More deatiled Information about this can be found in the following links: http://www.cs.ru.nl/~flaviog/publications/Attack.MIFARE.pdf
The Mifare Cracking GUI (mcgui) identifies, cracks, and clones both original and hardened Mifare Classic cards. Mcgui provides a simple user interface for existing Mifare cracking functions. The available cracking options through mcgui are the Dark Side , Hard Nested , and Nested attacks.In this Tradecraft tutorial, we will be decyphering and emulating Mifare Classic 1K cards using the Proxmark3 RDV4 and the RFID Tools Android App by RRG. Thi.
MIFARE, is a trademark for a series of chips widely used in contactless smart cards and proximity cards. It is often incorrectly used as a synonym of RFID. MIFARE is owned by NXP semiconductors which was previously known as Philips Electronics. The reason behind this misuse is simple. There’s plenty of guides online on how to crack the private keys that are supposed to make the card secure. Conveniently, [Guillermo] had a reader/writer on hand for these very cards..
• Initially utilize the MFOC tool to test if the card utilize any default keys. (around 10 minutes) – If the card utilizes any of default keys the MFOC tool will perform the Nested attack utilizing any authenticated sector as an exploit sector to recover all keys of the card and dump his content. First Key Recovery. CRYPTO-1 uses two 48 bits-long keys on Mifare Classic cards to encrypt the data on its sectors. Each key can be configured to be used for reading or writing on a sector. On. The first attack on Mifare cards is called Darkside attack, which exploit the weak pseudo-random generator on the card to discover a single key. This attack aims to recover one key from the.
How to Crack Mifare 1k RFID card. The NFC tag I analyzed is a so called “Mifare Classic 1k” tag. 1k stands for the size of data the tag can store. There are also other types like the “Mifare Classic 4k” and the “Mifare Mini” each having a different memory size. A Mifare Classic 1k tag contains 16 sectors. Each of these sectors has 3 .New Design RFID-PN532: https://shop.mtoolstec.com0:00 Quick look on the phone and card for testing.0:30 Read original data with Mifare Classic Tool0:56 Read . Mifare Classic in general is stated insecure, because it’s encryption protocol has been cracked. More deatiled Information about this can be found in the following links: http://www.cs.ru.nl/~flaviog/publications/Attack.MIFARE.pdfThe Mifare Cracking GUI (mcgui) identifies, cracks, and clones both original and hardened Mifare Classic cards. Mcgui provides a simple user interface for existing Mifare cracking functions. The available cracking options through mcgui are the Dark Side , Hard Nested , and Nested attacks.
playoff standings for the afc
Hacking Mifare Classic Cards
nfl standings east division
Hacking MIFARE & RFID
Touch the WRITE TAG (AUTO) button and press your NTAG215 NFC tag to your Android device. The stickers aren't re-writeable so I'd advise against trying that in the future so you don't mess the sticker up. Another ntag215 tag I recommend .
how to hack a mifare card|Cracking The MiFare Classic Could Get You Free Snacks