microsoft smart card deployment This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before . How to disable nfc reader on iphone. when the iphone comes into contact with nfc tags, the phone automatically notifies the popup to open the url in the browser. This happens .
0 · YubiKey Smart Card Deployment Guide – Yubico
1 · Smart Card Technical Reference
2 · Smart Card Group Policy and Registry Settings
3 · Microsoft Devices Security, Virtual Smart Cards Part 2: Deployment
Listen to Mad Dog Sports Radio (Ch 82), FOX Sports on SiriusXM (Ch 83), ESPN Radio (Ch 80), SiriusXM NASCAR Radio (Ch 90), and more. College Football is on SiriusXM. Get live .
The Smart Card Technical Reference describes the Windows smart card infrastructure for physical smart cards and how smart card-related components work in Windows. This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before . Discover the Group Policy, registry key, local security policy, and credential delegation policy settings that are available for configuring smart cards.In this article I covered the steps for preparing for deployment of Virtual Smart Cards, and how to manually deploy Virtual Smart Cards. In an upcoming posting, I will cover how to deploy .
A TPM virtual smart card simulates a physical smart card, using the TPM to provide the same functionality as physical smart card hardware. A virtual smart card appears within the operating system as a physical smart card that is always inserted.
The Smart Card Technical Reference describes the Windows smart card infrastructure for physical smart cards and how smart card-related components work in Windows. This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login.
Discover the Group Policy, registry key, local security policy, and credential delegation policy settings that are available for configuring smart cards.In this article I covered the steps for preparing for deployment of Virtual Smart Cards, and how to manually deploy Virtual Smart Cards. In an upcoming posting, I will cover how to deploy Virtual Smart Cards with FIM CM.Planning a Smart Card Deployment. Smart card support in Microsoft ® Windows ® Server 2003 enables you to enhance the security of many critical functions, including client authentication, interactive logon, and document signing, in your organization.This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise deployment, in addition to providing information necessary for .
YubiKey Smart Card Deployment Guide – Yubico
Next Steps. User Self Enrollment. Enrollment on Behalf of Other Users. Protecting Microsoft Cloud Environment with a YubiKey. Configuring a Certification Authority (CA) for Smart Card Authentication. The phishing-resistant passwordless deployment approach commonly has 6 steps, which roughly flow in order, but don't have to be 100% completed before moving on to other steps: Determine your user personas. Determine the user personas relevant for your organization. Before You Begin. The YubiKey Minidriver is designed to function in a Windows Server and Client environment configured for smart card authentication. Ensuring your deployment is set up properly is a crucial element of the .
A TPM virtual smart card simulates a physical smart card, using the TPM to provide the same functionality as physical smart card hardware. A virtual smart card appears within the operating system as a physical smart card that is always inserted. The Smart Card Technical Reference describes the Windows smart card infrastructure for physical smart cards and how smart card-related components work in Windows. This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login. Discover the Group Policy, registry key, local security policy, and credential delegation policy settings that are available for configuring smart cards.
In this article I covered the steps for preparing for deployment of Virtual Smart Cards, and how to manually deploy Virtual Smart Cards. In an upcoming posting, I will cover how to deploy Virtual Smart Cards with FIM CM.
Planning a Smart Card Deployment. Smart card support in Microsoft ® Windows ® Server 2003 enables you to enhance the security of many critical functions, including client authentication, interactive logon, and document signing, in your organization.
This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise deployment, in addition to providing information necessary for . Next Steps. User Self Enrollment. Enrollment on Behalf of Other Users. Protecting Microsoft Cloud Environment with a YubiKey. Configuring a Certification Authority (CA) for Smart Card Authentication.
rise rfid nfc blocking card
The phishing-resistant passwordless deployment approach commonly has 6 steps, which roughly flow in order, but don't have to be 100% completed before moving on to other steps: Determine your user personas. Determine the user personas relevant for your organization.
nfl standings wild card nfc
Smart Card Technical Reference
Smart Card Group Policy and Registry Settings
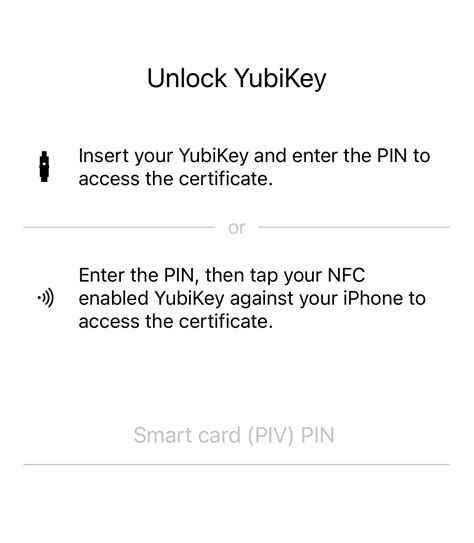
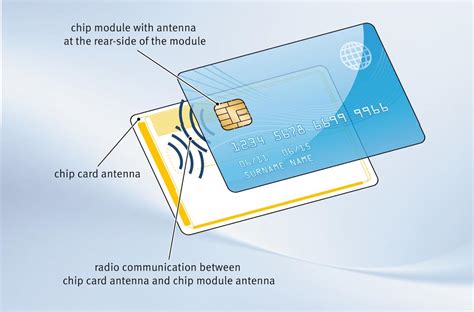
The NFC-capable hardware security keys from Yubico (YubiKey 5 NFC, YubiKey 5C NFC, YubiKey 5 NFC FIPS, YubiKey 5C NFC FIPS, Security Key NFC, Security Key C NFC) provide an NFC wireless interface in addition to USB.
microsoft smart card deployment|YubiKey Smart Card Deployment Guide – Yubico