hight range rfid stealing card devices You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you.
Watch game highlights from the NFC Wild Card playoff matchup between the Green Bay Packers and Dallas Cowboys at AT&T Stadium. Take a look at the best plays from the Green Bay Packers through the .
0 · rfid wallet scam
1 · rfid snoop card hack
2 · rfid shielding
3 · rfid scanners for criminals
4 · rfid scam
5 · rfid chip
6 · rfid blocking cards
7 · cell phone rfid scanner
The workaround for iOS: upload your .vcf file to a publicly-accessible link. This can be on .
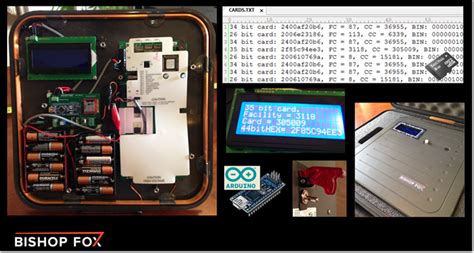
November 3, 2013. Security researcher [Fran Brown] sent us this tip about his Tastic RFID Thief, which can stealthily snag the information off an RFID card at long range. If you’ve worked with.
The capacitor doesn’t split the voltage. It limits the current. Line power is 60Hz. You just hav. RFID cards and tags can be rendered useless by hackers who generate a .
Modern payment cards have a built in chip that transmits card information wirelessly. This is because it is necessary in order to enable contactless payments, which has become increasingly popular during recent years. Criminals can take advantage of this new technology by using a scanner that wirelessly scans the victim's payment card in the same way that a cash register scans it, when making a contactless payment. These scanners are legal and can be bought in r.November 3, 2013. Security researcher [Fran Brown] sent us this tip about his Tastic RFID Thief, which can stealthily snag the information off an RFID card at long range. If you’ve worked with.
You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you. RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos by blocking access with ID cards.RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in chip that transmits card information wirelessly.The Tastic RFID Thief is a silent, long-range RFID reader that can steal the proximity badge information from an unsuspecting employee as they physically walk near this concealed device. Specifically, it is targeting 125KHz, low frequency RFID badge systems used for physical security, such as those used in HID Prox and Indala Prox products.
RFID scanners that capture and record ID information are certainly not legal, but for those with the proper skills, they’re easy to build. Hackers use a long-range reader to silently steal this ID info from any RFID cards that happen to walk by.
Hackers using RFID scanners can theoretically steal money via your phone's tap-to-pay app. Here's how to prevent RFID hacking.NFC/RFID skimming is where hackers/skimmers/bad guys intercept the radio wave communication between devices or simply read the radio waves that a NFC or RFID enabled device puts out. The bad guy's reader reads the data put out from your device or debit/credit card.Despite its many benefits, RFID technology is vulnerable to hacking in several ways. First, RFID signals can be intercepted, allowing an attacker to eavesdrop on sensitive data. Second, attackers can use a high-powered reader to forcibly power up a tag that has been turned off to steal its data.
Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from "skimming" the.
November 3, 2013. Security researcher [Fran Brown] sent us this tip about his Tastic RFID Thief, which can stealthily snag the information off an RFID card at long range. If you’ve worked with. You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you. RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos by blocking access with ID cards.RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in chip that transmits card information wirelessly.
The Tastic RFID Thief is a silent, long-range RFID reader that can steal the proximity badge information from an unsuspecting employee as they physically walk near this concealed device. Specifically, it is targeting 125KHz, low frequency RFID badge systems used for physical security, such as those used in HID Prox and Indala Prox products. RFID scanners that capture and record ID information are certainly not legal, but for those with the proper skills, they’re easy to build. Hackers use a long-range reader to silently steal this ID info from any RFID cards that happen to walk by. Hackers using RFID scanners can theoretically steal money via your phone's tap-to-pay app. Here's how to prevent RFID hacking.
nabber smart card manager
NFC/RFID skimming is where hackers/skimmers/bad guys intercept the radio wave communication between devices or simply read the radio waves that a NFC or RFID enabled device puts out. The bad guy's reader reads the data put out from your device or debit/credit card.Despite its many benefits, RFID technology is vulnerable to hacking in several ways. First, RFID signals can be intercepted, allowing an attacker to eavesdrop on sensitive data. Second, attackers can use a high-powered reader to forcibly power up a tag that has been turned off to steal its data.

rfid wallet scam
This app emulates an NFC Forum Type 4 Tag on an Android device using Host-based Card Emulation ("HCE").. To be compliant with the specification a service is running independent on the app opened that serves an Application Identifier .
hight range rfid stealing card devices|rfid blocking cards