smart card authentication architecture Learn how 1Kosmos enhances smart card authentication with BlockID, offering . The easiest way to share contact info. Comes with free profile. Makes a bold statement with metal appearance and sleek design. Similar feel to Apple Card. .Introducing VistaConnect – a free service that adds an online extension to a single business card you keep. Smart scanning technology instantly brings customers to schedules, signup forms and everything else that makes your business go. See our guide. See more
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
How to Hack a Bus Pass for Practical Wearable Tech #WearableWednesday #wearabletech #DIY. Transit passes often take the form of cards, whether they be swipe or NFC (Near Field Communication). They are .
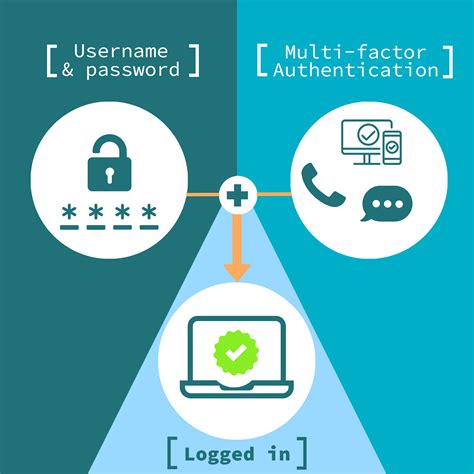
Vendors provide smart cards and smart card readers, and in many cases the vendors are different for the smart card and the smart card reader. Drivers for smart . See moreSmart Card Architecture: Learn about enabling communications with smart cards and smart . Smart cards are tamper-resistant portable storage devices that can enhance the . Learn how 1Kosmos enhances smart card authentication with BlockID, offering .
Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits . Smart cards could help automate and standardize patient demographic . This topic for the IT professional describes the system architecture that supports smart cards in the Windows operating system, including credential provider architecture and the smart card subsystem architecture. Authentication is a process for verifying the identity of an object or person.Smart Card Architecture: Learn about enabling communications with smart cards and smart card readers, which can be different according to the vendor that supplies them.
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
smart card multi factor authentication
Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data. Smart cards could help automate and standardize patient demographic information on medical records, including those of insurance carriers. Smart cards with optical storage could store and transfer both text and image-based medical records between patient and . Abstract. Smart cards have been widely used as simple token hardware in authenticationn processes. Nevertheless, a new trend indicates a shift towards more enhanced cards with networking capabilities. We propose revising the usual focus on smart card authentication protocol designs, as well as highlighting the need to adapt to new trends.Smart card authentication is perhaps the best-known example of a proof by possession mechanism. Other classes of authentication mechanisms include proof by knowledge (e.g., passwords) and proof by property (e.g., fingerprints).
Properly coded smart card applications will keep sensitive memory space away from all other applications and prevent private keys from being accessible to outside processes. Java Card. Java Card has become a pervasive platform for .This Personal Identity Verification (PIV) 101 is intended to help you understand the purpose and uses of a PIV credential at your organization. This PIV 101 focuses on using PIV credentials for logical access such as authenticating to networks or .
This topic for the IT professional describes the system architecture that supports smart cards in the Windows operating system, including credential provider architecture and the smart card subsystem architecture. Authentication is a process for verifying the identity of an object or person.Smart Card Architecture: Learn about enabling communications with smart cards and smart card readers, which can be different according to the vendor that supplies them. Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account.
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data. Smart cards could help automate and standardize patient demographic information on medical records, including those of insurance carriers. Smart cards with optical storage could store and transfer both text and image-based medical records between patient and .
Abstract. Smart cards have been widely used as simple token hardware in authenticationn processes. Nevertheless, a new trend indicates a shift towards more enhanced cards with networking capabilities. We propose revising the usual focus on smart card authentication protocol designs, as well as highlighting the need to adapt to new trends.Smart card authentication is perhaps the best-known example of a proof by possession mechanism. Other classes of authentication mechanisms include proof by knowledge (e.g., passwords) and proof by property (e.g., fingerprints).
smart card identity
Properly coded smart card applications will keep sensitive memory space away from all other applications and prevent private keys from being accessible to outside processes. Java Card. Java Card has become a pervasive platform for .

smart card based identification system
smart card authentication step by
We print cards with variable fields, such as ID badges with personal photos, at no extra charge. Variable printing can include: text fields, images, QR code, bar codes, progressive numbers. To make variable printing, you need to send us: 1. an Excel file with a column for . See more
smart card authentication architecture|smart card authentication protocol