how does an rfid chip protection work The encoding process in RFID relies on magnetization in specific patterns that can be picked up when they are unshielded, but many new products use a combination of carbon fiber and aluminum, contained in an appealing case, to .
Hyundai uses some secure encryption of the NFC tags. I've tried copying the original NFC card .
0 · what is meant by rfid
1 · rfid is involved when using
2 · rfid definition computer
3 · radio frequency identification rfid tag
4 · radio frequency identification examples
5 · radio frequency identification chips
6 · how does rfid scanning work
7 · how do rfid cards work
Actually making them. It’s very simple. Activate NFC on your phone. Make sure you have the unfixed-info and locked-secret bins already loaded in (reference the guide above for help). Open Tagmo, and press “Load .
Passports and some credit cards have RFID chips that allow information to be read wirelessly. . RFID-blocking wallets have card sleeves (or sometimes entire wallets) made from materials that don't let radio waves through. That way, the chip won't power up, and even if it did, its signal wouldn't get through the wallet.
Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from. An RFID chip is used to exchange information with an RFID reader using radio waves. Depending on the RFID chip — active or passive — these radio waves can broadcast from only a few inches to upwards of 1,500 feet. What is RFID-Blocking tech? It protects your personal data from hackers by providing a buffer that blocks others from skimming the chip on your credit cards.
The encoding process in RFID relies on magnetization in specific patterns that can be picked up when they are unshielded, but many new products use a combination of carbon fiber and aluminum, contained in an appealing case, to . RFID blocking is the process of making your RFID-enabled device resistant to unauthorized access. The most popular way to achieve this is by getting an RFID blocking wallet — a holder for your cards that is made from materials that interfere with electromagnetic fields. How does RFID skimming work? RFID or radio frequency identification is a form of wireless communication. RFID chips are sometimes used in passports, credit cards, and transport passes. Can an RFID blocking card keep someone from "reading" your card without your knowledge? I put it to the test. Credit and debit cards contain RFID contactless technology.
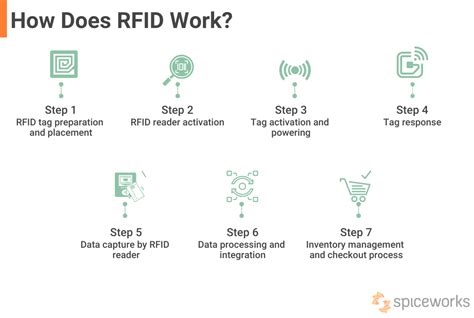
How does RFID work? An RFID system is composed of three key components: an antenna, a transceiver, and a transponder. It’s through the combination of the antenna and transceiver that you get an RFID reader. This network-connected device may be fixed such as in the case of an airport passport reader. RFID chips work by using radio waves to communicate. The object, such as a credit card, contains an RFID tag with information, and an RFID reader uses radio waves to read the information off that tag.
RFID-blocking wallets have card sleeves (or sometimes entire wallets) made from materials that don't let radio waves through. That way, the chip won't power up, and even if it did, its signal wouldn't get through the wallet. Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from. An RFID chip is used to exchange information with an RFID reader using radio waves. Depending on the RFID chip — active or passive — these radio waves can broadcast from only a few inches to upwards of 1,500 feet.
What is RFID-Blocking tech? It protects your personal data from hackers by providing a buffer that blocks others from skimming the chip on your credit cards. The encoding process in RFID relies on magnetization in specific patterns that can be picked up when they are unshielded, but many new products use a combination of carbon fiber and aluminum, contained in an appealing case, to .
RFID blocking is the process of making your RFID-enabled device resistant to unauthorized access. The most popular way to achieve this is by getting an RFID blocking wallet — a holder for your cards that is made from materials that interfere with electromagnetic fields. How does RFID skimming work? RFID or radio frequency identification is a form of wireless communication. RFID chips are sometimes used in passports, credit cards, and transport passes. Can an RFID blocking card keep someone from "reading" your card without your knowledge? I put it to the test. Credit and debit cards contain RFID contactless technology.
what is meant by rfid
How does RFID work? An RFID system is composed of three key components: an antenna, a transceiver, and a transponder. It’s through the combination of the antenna and transceiver that you get an RFID reader. This network-connected device may be fixed such as in the case of an airport passport reader.
amiibo action replay nfc card
rfid is involved when using

rfid definition computer
$64.00
how does an rfid chip protection work|radio frequency identification examples