do rfid chips have security features Learn how RFID chips in electronic IDs are protected from unauthorized access and forgery. Explore advanced security measures like PACE, EAC, and chip authentication. We take a deep dive into the electronic identity documents and unveil how our sensitive personal data is protected in RFID chips.
$19.99
0 · what is rfid technology
1 · what is rfid security
2 · what is rfid protection
3 · what is rfid card
4 · rfid enabled credit cards
5 · rfid blocking chips
6 · do you need rfid protection
7 · are rfid tags safe
Information about reward points, offers, discounts and much more on indian credit card spends. Samsung wallet is one of the best wallet to have. Those who have Samsung phones with NFC try using Samsung wallet, It is one of the fastest .
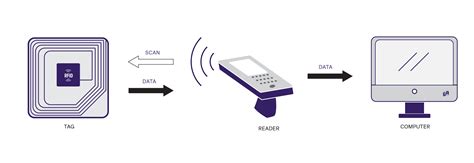
what is rfid technology
What is RFID-Blocking tech? It protects your personal data from hackers by providing a buffer that blocks others from skimming the chip on your credit cards. They're also used for transit systems, tolls, and security access cards. They can be read by a machine with a quick tap. Many household pets also have RFID chips embedded in them. If your dog or cat is "chipped," it has a small microchip injected between its shoulder blades. What is RFID-Blocking tech? It protects your personal data from hackers by providing a buffer that blocks others from skimming the chip on your credit cards.
The advantages of using RFID chips include improved accuracy when compared with manual methods such as barcodes; increased speed when scanning multiple items; reduced labor costs; improved security since they cannot be easily copied or counterfeited; increased visibility into inventory levels; better customer service since customers can quickly .
what is rfid security
what is rfid protection
Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from "skimming". Learn how RFID chips in electronic IDs are protected from unauthorized access and forgery. Explore advanced security measures like PACE, EAC, and chip authentication. We take a deep dive into the electronic identity documents and unveil how our sensitive personal data is protected in RFID chips. However, the use of RFID chips raises concerns about privacy and security. As RFID technology allows for remote scanning, there have been apprehensions about unauthorized data access and tracking individuals without their consent. Privacy measures and encryption protocols are essential to address these concerns and protect sensitive information.
If you’re interested in the NXP ICODE® chip series or looking for RFID solutions, this article is a must-read reference. This guide will dive deep into the key features, common application scenarios, and unique advantages of the NXP ICODE® chip series, showing how it can help industries around the globe improve operational efficiency and enhance security by providing .
Throughout this article, we have explored the various security risks of RFID technology, including unauthorized access, eavesdropping, cloning and forgery, and denial of service attacks. In short, RFID technology has existed for many decades, but even modern cards can pose a huge vulnerability in your RFID-based security environment if not implemented well. The main risks are that attackers can gain access to your premise through cloning, replaying, relaying and brute-force attacks. RFID blocking tools claim to protect users against identity theft by stopping criminals from scanning your passport’s ID chip by just rubbing shoulders with you. In practice, however, RFID blocking does little to help in the most likely identity theft scenarios.
They're also used for transit systems, tolls, and security access cards. They can be read by a machine with a quick tap. Many household pets also have RFID chips embedded in them. If your dog or cat is "chipped," it has a small microchip injected between its shoulder blades. What is RFID-Blocking tech? It protects your personal data from hackers by providing a buffer that blocks others from skimming the chip on your credit cards.
smart card terminal hp
The advantages of using RFID chips include improved accuracy when compared with manual methods such as barcodes; increased speed when scanning multiple items; reduced labor costs; improved security since they cannot be easily copied or counterfeited; increased visibility into inventory levels; better customer service since customers can quickly .
Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from "skimming". Learn how RFID chips in electronic IDs are protected from unauthorized access and forgery. Explore advanced security measures like PACE, EAC, and chip authentication. We take a deep dive into the electronic identity documents and unveil how our sensitive personal data is protected in RFID chips. However, the use of RFID chips raises concerns about privacy and security. As RFID technology allows for remote scanning, there have been apprehensions about unauthorized data access and tracking individuals without their consent. Privacy measures and encryption protocols are essential to address these concerns and protect sensitive information.If you’re interested in the NXP ICODE® chip series or looking for RFID solutions, this article is a must-read reference. This guide will dive deep into the key features, common application scenarios, and unique advantages of the NXP ICODE® chip series, showing how it can help industries around the globe improve operational efficiency and enhance security by providing .
Throughout this article, we have explored the various security risks of RFID technology, including unauthorized access, eavesdropping, cloning and forgery, and denial of service attacks. In short, RFID technology has existed for many decades, but even modern cards can pose a huge vulnerability in your RFID-based security environment if not implemented well. The main risks are that attackers can gain access to your premise through cloning, replaying, relaying and brute-force attacks.
what is rfid card
Ricoh NFC Card Reader Type M19 (417573) Part Number: RIC417573. NFC Card Reader .Used to login and authenticate users via NFC card. The card reader and its cable will be .
do rfid chips have security features|are rfid tags safe